The gas challenge on Ethereum
“Oh boy, a really cool project airdropped a token on my Ethereum wallet and now unfortunately I cannot transfer it to my main wallet because I do not have any ether on this address. That really sucks!”
If this sounds familiar to you, you can skip the next section. However, if the whole thing sounds cryptic to you, here is a brief explanation of the gas challenge on Ethereum.
Gas is pivotal in the Ethereum world. To make the analogy, it is the fuel that allows it to operate, in the same way, that a car needs gasoline to run. In summary, gas refers to the unit that measures the amount of computational effort required to execute specific operations (e.g. sending ether (ETH) or a token) on the Ethereum network. Since each Ethereum transaction requires computational resources to execute, each transaction requires a fee (=commonly known as the multiple of gas price and gas consumed by the transaction). Gas fees are paid in Ethereum's native currency ETH. Also, gas prices are usually denoted in a unit called gwei, which itself is a denomination of ETH – each gwei is equal to 0.000000001 ETH (or 10-9 ETH). For instance, instead of saying that your gas costs 0.000000001 ETH, you would usually say that your gas costs 1 gwei. The word gwei itself means giga-wei and it is equal to 1’000’000’000 wei (1 wei = 10-18 ETH). Wei itself – named after Wei Dai, the inventor of b-money – is the smallest unit of ETH.
But why do gas fees actually exist? In short, gas fees help keep the Ethereum network secure. By requiring a fee for every computation executed on the network, we prevent bad actors from spamming the network. For a further deep-dive into this topic, I can recommend this reference.
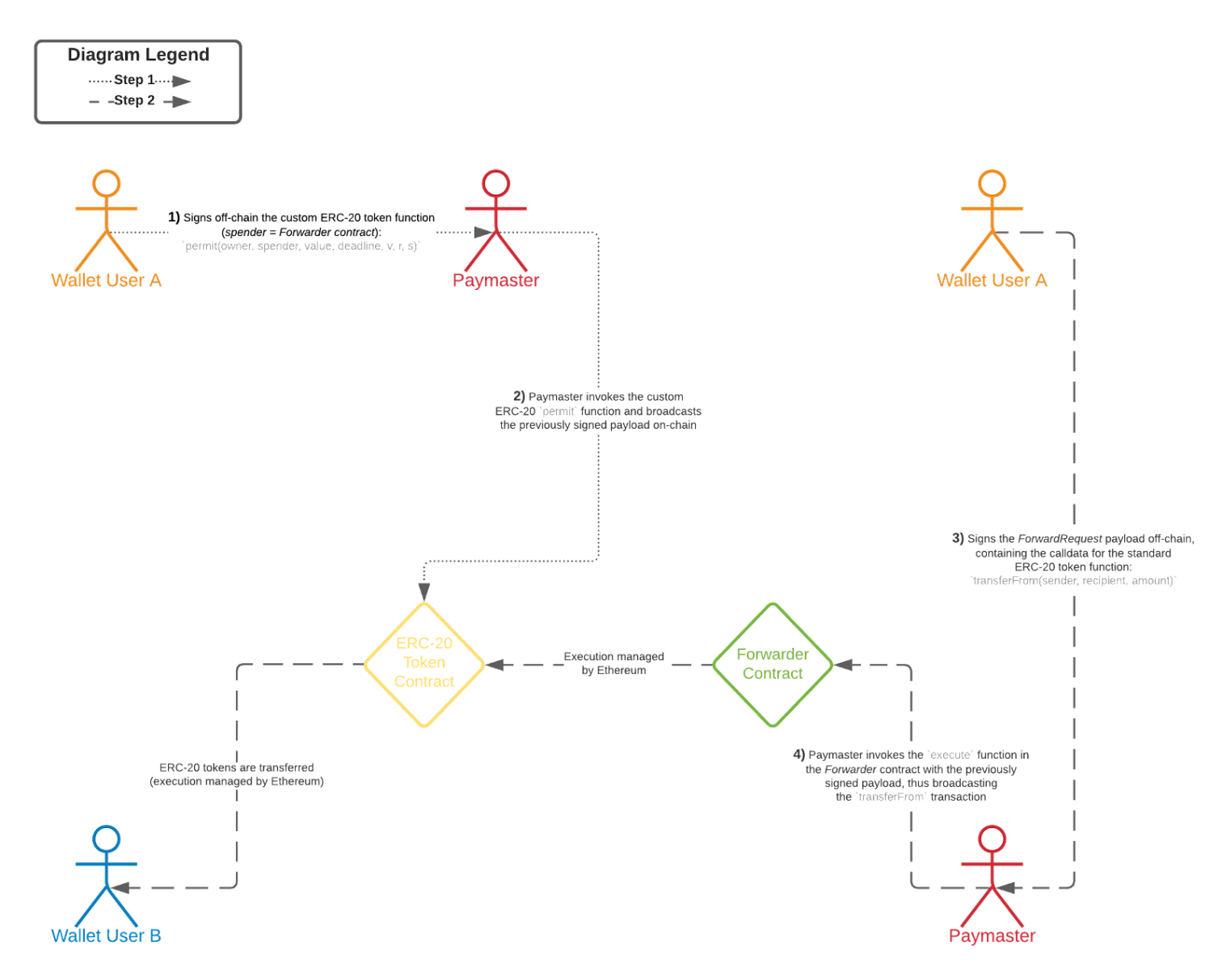
So what we have learned so far is that every (write) interaction on the Ethereum blockchain requires a small amount of ETH on the interacting address. This sounds really awful from a UX perspective for token holders, as users first need to acquire ETH via a centralised exchange and transfer it to the wallet address accordingly. But wait, isn't it the case – very simplified – that at the most foundational blockchain level, it is simply a matter of verifying the signed payload, i.e. off-chain cryptography? Ah yes, that sounds right! So how about the wallet user simply signs the payload off-chain and someone else (e.g. an operator) broadcasts and pays for the transaction? There you go, we have the solution: meta-transactions.